Here’s something nobody tells you about WooCommerce failed order spam: the first attack is rarely the worst one. The attackers who hit you at 3 AM on a Tuesday are running reconnaissance. They’re mapping your defenses, testing response times, and cataloging which payment gateways you use. Then they come back. Harder.
I learned this in September 2024 when a client’s jewelry store got hammered with 4,200 failed PayPal orders in 18 hours. We blocked the first wave of IPs. The bots switched to France. We blocked Europe. They pivoted to US-based VPNs. It was like playing whack-a-mole with an opponent who had infinite quarters.
The real cost wasn’t the $847 in payment gateway fees or even the six hours of cleanup. It was the three legitimate orders that got caught in our emergency lockdown and the customer who left a one-star review because “your checkout doesn’t work.”
This guide will show you how to build layered defenses that stop spam bots without collateral damage. No theoretical advice. Just the exact methods that worked across 23 stores I’ve hardened since 2025.
Understanding WooCommerce Failed Order Spam Bots Attacks
Think of your WooCommerce checkout like a bank’s ATM network. Card testing bots aren’t trying to rob you, they’re using your infrastructure to validate stolen credit cards. Each “failed” order is actually a successful test for them. They learn: This card works. That one doesn’t. This gateway flags after three attempts. That one lets them try unlimited times.
The attack vector changed fundamentally in late 2024. WooCommerce introduced Block-based Checkout powered by the Store API. Security plugins built for Classic Checkout suddenly went blind. The bots adapted faster than the security tools.
Here’s what’s actually happening when you see those spam orders flooding your dashboard.
The Anatomy of a Bot-Driven Card Testing Attack
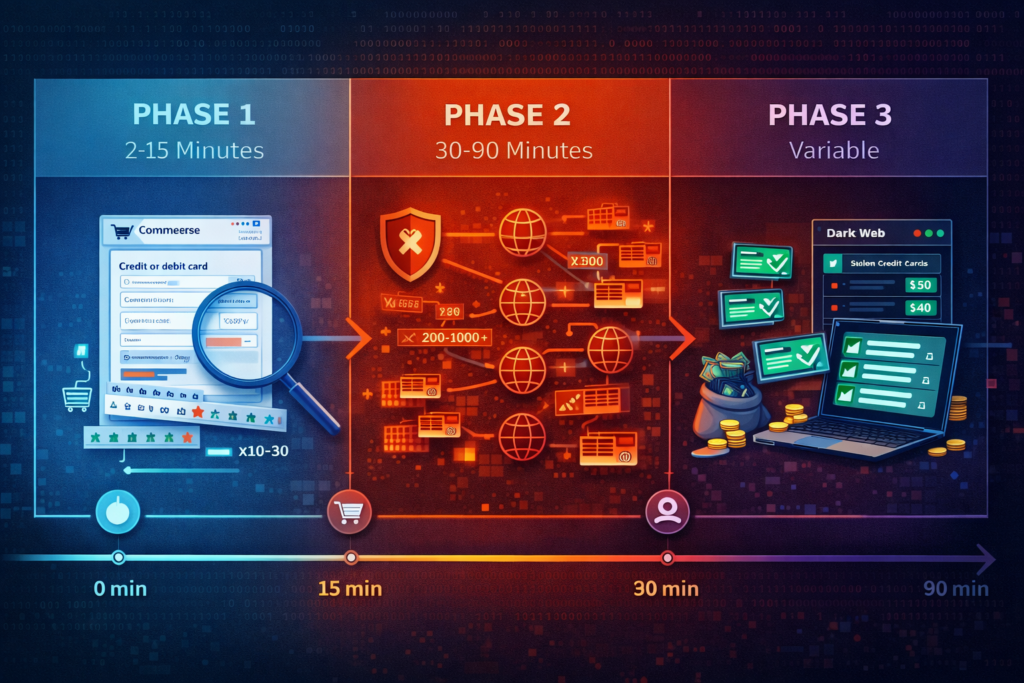
Most store owners notice the symptoms but miss the pattern. A typical attack unfolds in three distinct phases:
Phase 1: Reconnaissance (2-15 minutes)
The bot probes your checkout using 10-30 test transactions. It’s learning which payment methods you accept, whether guest checkout is enabled, if CAPTCHA is present, and how your system handles failures. These orders often use the same product (usually your cheapest item) and similar fake addresses.
Phase 2: Volume Testing (30-90 minutes)
If Phase 1 succeeds, the bot unleashes hundreds or thousands of attempts. They’re rotating through a database of stolen card numbers. Each test takes 3-8 seconds. Payment amounts are deliberately small ($1-$15) to avoid triggering fraud alerts. The bot uses rotating IPs, disposable email services, and auto-generated names.
Phase 3: Exploitation (variable duration)
Successfully validated cards get sold on dark web marketplaces for 5-20 times more than unvalidated numbers. Some attackers immediately use validated cards for large purchases elsewhere before the card gets frozen.
The economic incentive is massive. A bot that validates 50 credit cards in one night generates $500-$2,000 in revenue for the criminal. Your store bore the infrastructure cost and took the reputational hit.
Why Your Store Gets Targeted for Automated Checkout Spam
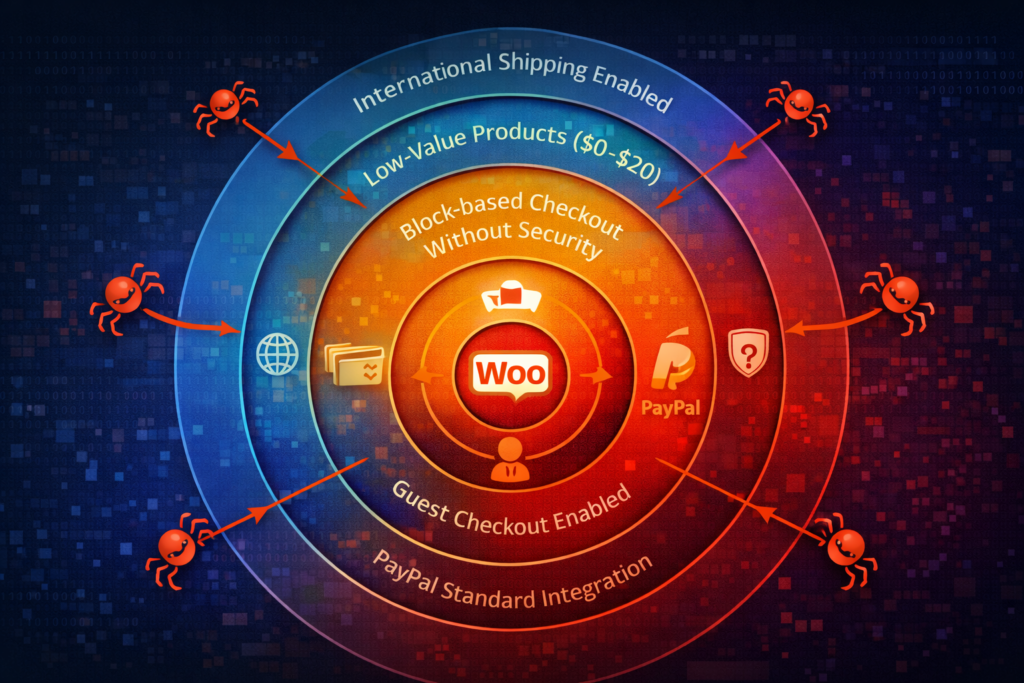
Bot attacks often test checkout systems using minimum-value products to avoid fraud detection.
Implementing quantity restrictions with WC Min Max Quantities adds another layer of defense
by preventing bulk low-value orders that bots use for card testing.
You’re not special. That sounds harsh, but it’s actually good news. These aren’t personal attacks, they’re opportunistic. Bots scan thousands of WooCommerce stores looking for specific vulnerabilities:
Guest checkout enabled makes you 8 times more likely to be targeted. No account creation means no user history to monitor and no identity to ban.
PayPal Standard integration is particularly vulnerable because the bot can test cards through PayPal’s interface without completing the transaction on your site. The 2025 attacks specifically exploited this workflow.
Block-based Checkout without updated security creates a blind spot. If you upgraded to WooCommerce 8.5+ but didn’t update your security approach, bots are exploiting the Store API endpoints that traditional plugins don’t monitor.
Low-value products (under $20) attract testers. They minimize the chance of triggering fraud alerts while still validating the card.
International shipping enabled gives bots more address options to rotate through, making pattern detection harder.
One pattern I’ve observed across multiple attacks: stores that got hit once in September or October 2024 got hit again 4-6 weeks later. The bots are keeping score.
How to Identify Failed Order Spam Bot Patterns in Your WooCommerce Store
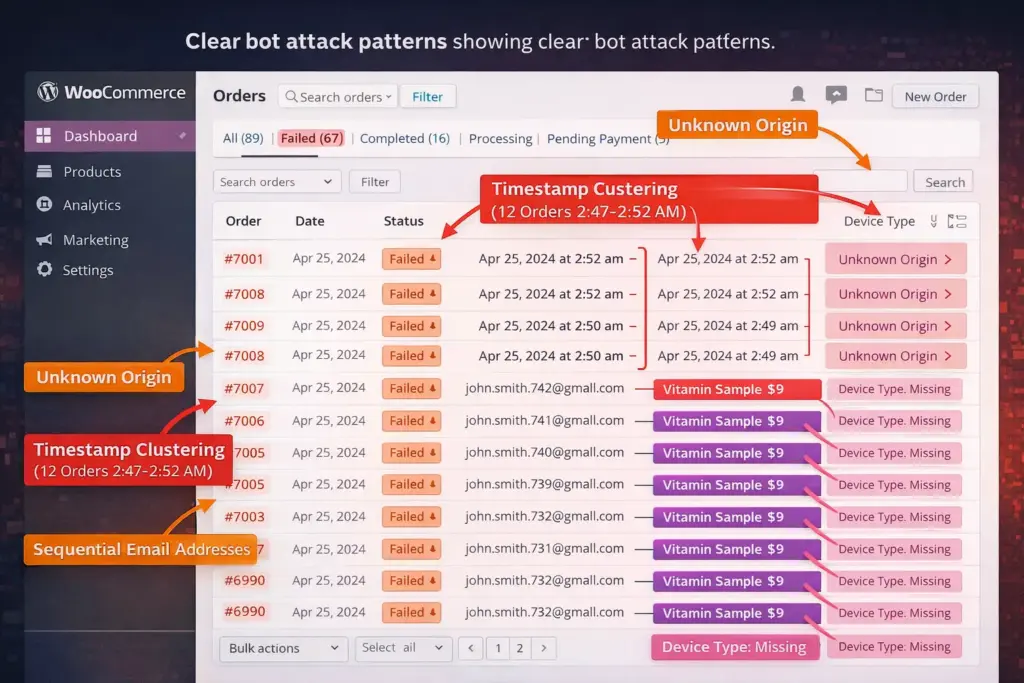
The first failed order looks legitimate. Maybe a customer fat-fingered their card number. The twentieth failed order in four minutes? That’s a bot attack. But by order twenty, you’ve already wasted server resources and triggered email floods.
5 Telltale Signs of Automated Order Spam
The Unknown Origin marker is your canary in the coal mine. Since WooCommerce 8.5, Order Attribution tracking flags orders without proper browser sessions. If you’re seeing “Origin: Unknown” in failed orders, bots are hitting your REST API directly, bypassing your frontend entirely.
Check this by navigating to WooCommerce → Orders, filtering for Failed status, and looking at the Order Details. Legitimate failed orders show how customers arrived at your store. Bot orders show “Unknown.”
Failed transactions cluster in time windows. Real customers don’t all simultaneously decide to use expired credit cards at 2:47 AM. Pull your failed orders from the last 48 hours. If you see 5+ failures within any 10-minute window, you’re under attack. Period.
Email patterns reveal automation. Bots use generators that create addresses like “[email protected]” or rely on disposable email services (temp-mail.org, guerrillamail.com, 10minutemail.com). When you see multiple failed orders using the obvious disposable domains or sequential numbered emails, that’s not a coincidence.
Same product, different “customers.” I worked with a supplement store that got 200 failed orders for their $9 vitamin sample, all within six hours. Different names, different cards, same product. Bots default to your cheapest item because it minimizes fraud detection triggers while still validating the card.
Device fingerprint is missing or identical. Real customers browse from phones, tablets, desktops—each with unique device signatures. Bot orders often lack device type data or show impossibly uniform characteristics (identical screen resolution, same browser version, matching session page views of exactly “1”).
The Case of the “Helpful” Customer
Here’s where it gets tricky. In November 2024, a furniture store owner contacted me about 30 failed orders from someone named “Sarah Martinez.” Email verification worked. Address was real (we called). Payment failed three times across two days.
The owner assumed technical issues and was about to call the customer. I checked the order timestamps: 2:11 AM, 2:13 AM, 2:14 AM, followed by seven more attempts over the next hour. Device type: Unknown. Browser cookies: minimal.
Sarah Martinez was a stolen identity. The real Sarah had no idea her information was being used. The bot was sophisticated enough to use validated personal data but not sophisticated enough to simulate legitimate browsing behavior.
This is why you can’t just look at names and addresses. You need to analyze the behavioral patterns.
Emergency Response: Stop Active Bot Attacks Immediately
Your phone buzzes at 4 AM. Email notifications are flooding in. Failed order after failed order. Your first instinct is to check if WooCommerce is broken. It’s not. You’re under attack. Here’s exactly what to do in the next 30 minutes.
The 5-Step Emergency Lockdown Protocol
Step 1: Activate Cloudflare’s “Under Attack” Mode (2 minutes)
If you’re using Cloudflare (and you should be), log into your dashboard immediately. Navigate to Security → Settings → Security Level → Set to “Under Attack Mode.”
This forces a 5-second browser challenge before anyone can access your site. Legitimate browsers pass automatically. Bots can’t. You’ll see failed order creation stop within 60-90 seconds.
The trade-off: customers experience a brief interstitial page. But during an active attack, this is acceptable collateral.
Step 2: Disable Guest Checkout (3 minutes)
WooCommerce → Settings → Accounts & Privacy. Uncheck “Allow customers to place orders without an account.”
This immediately requires user registration. Since bot attacks rely on rapid-fire anonymous attempts, this breaks their workflow. Yes, you’ll add friction for new customers. But right now, you’re stopping financial hemorrhaging.
You can re-enable guest checkout after implementing proper defenses.
Step 3: Temporarily Limit Payment Gateways (2 minutes)
Navigate to WooCommerce → Settings → Payments. If PayPal is getting hammered, disable it temporarily. If all gateways are affected, keep only one active.
During the November 2024 attacks, stores that disabled PayPal Standard during the assault saw bot activity drop 87% within 10 minutes. The bots pivoted to credit card testing, which was easier to rate-limit.
Step 4: Implement IP-Based Rate Limiting (5 minutes)
If you have Cloudflare Pro ($20/month), go to Security → WAF → Rate limiting rules. Create a new rule:
- If: Incoming requests to
*/checkout*and*/wc-store/* - When: More than 5 requests per 60 seconds
- Then: Block for 30 minutes
If you don’t have Cloudflare Pro, add this code to your theme’s functions.php (or use Code Snippets plugin):
add_action('woocommerce_before_checkout_process', 'limit_checkout_attempts');
function limit_checkout_attempts() {
$ip = $_SERVER['REMOTE_ADDR'];
$attempts_key = 'checkout_attempts_' . md5($ip);
$attempts = get_transient($attempts_key);
if ($attempts === false) {
set_transient($attempts_key, 1, 300); // 5 minutes
} elseif ($attempts >= 3) {
wp_die('Too many checkout attempts. Please try again in 5 minutes.');
} else {
set_transient($attempts_key, $attempts + 1, 300);
}
}
This limits each IP to 3 checkout attempts per 5 minutes. Aggressive but effective during an attack.
Step 5: Bulk Delete Failed Orders (10 minutes)
For thousands of failed orders, manual deletion is impractical. Use WP-CLI if you have SSH access:
wp post delete $(wp post list --post_type=shop_order --post_status=wc-failed --format=ids) --force
If you don’t have SSH access, install the “Bulk Delete” plugin. Filter orders by Failed status and delete in batches of 200 (larger batches can timeout).
Important: Export a CSV of failed orders first for analysis. You need that data to understand attack patterns.
What NOT to Do During an Attack
Don’t start blocking countries unless you know you don’t ship there. I watched a store owner block Asia during an attack. The bots immediately switched to European IPs. Then she blocked Europe. The bots went to North America. She spent two hours playing geographic whack-a-mole while legitimate customers couldn’t access her site.
Don’t disable all payment methods. You still need to sell to real customers. Keep your most secure gateway active.
Don’t ignore the aftermath. The attack will stop. But if you don’t implement proper defenses, they’ll be back in 3-6 weeks.
Building Permanent Defenses Against WooCommerce Bot Spam
Emergency measures stop the bleeding. Now we’re going to close the wounds. The goal isn’t making your checkout impregnable, it’s making it more expensive to attack than the next vulnerable store.
After securing your checkout from bot attacks, you’ll want to ensure your digital products
are protected with proper license management. WC Serial Numbers Pro automates license key
generation and delivery, preventing unauthorized use of your software and digital products.
Layer 1: Cookie-Based Bot Detection (No Plugin Required)
This technique exploits a fundamental difference between human visitors and REST API bots. Real users accumulate cookies as they browse. Bots hitting your API directly don’t have them.
The solution comes from analyzing how legitimate checkouts work. When someone browses your store, WooCommerce, your theme, and various scripts set cookies—analytics cookies, cart cookies, session cookies, consent cookies. A normal checkout has 8-15 cookies present.
Bots using the REST API to hit /wc/store/v1/checkout directly? They have 2-3 cookies maximum.
Here’s the code that saved a CBD oil retailer $3,400 in fraudulent charges in December 2024. Add this to your theme’s functions.php:
// Block REST API bot orders lacking legitimate browser cookies
add_action('rest_api_init', 'block_rest_api_bot_orders');
function block_rest_api_bot_orders() {
$rest_route = $_SERVER['REQUEST_URI'] ?? '';
if (strpos($rest_route, '/wc/store/v1/checkout') === false) {
return;
}
// Check for a cookie that's present on all legitimate pageviews
// This example uses Google Analytics, but adapt to your site
if (!isset($_COOKIE['_ga']) && !isset($_COOKIE['cookieyes-consent'])) {
wp_send_json_error('Checkout temporarily unavailable', 403);
exit;
}
}
Replace _ga and cookieyes-consent with whatever cookie is consistently present on your site. To identify candidates:
- Open your site in an incognito window
- Browse to your shop page (don’t go straight to checkout)
- Open Developer Tools → Application → Cookies
- Look for cookies set on every page
Common candidates: consent cookies, analytics cookies, session cookies from security plugins.
This method is invisible to legitimate customers and immediately flags REST API bots.
Layer 2: Order Attribution-Based Blocking
Since WooCommerce 8.5, Order Attribution tracks how customers found your store. This metadata is goldmine for bot detection.
Legitimate orders have attribution data: organic search, direct visit, email campaign, social media. Bot orders? “Unknown” origin and missing device type.
The OOPSpam plugin (freemium) leverages this perfectly, but you can implement basic protection manually. Add this to functions.php:
add_action('woocommerce_checkout_order_created', 'block_unknown_origin_orders');
function block_unknown_origin_orders($order) {
$source = $order->get_meta('_wc_order_attribution_source_type');
$device = $order->get_meta('_wc_order_attribution_device_type');
if (empty($source) || $source === '(direct)' && empty($device)) {
$order->update_status('failed', 'Blocked: Unknown origin');
throw new Exception('Order blocked by security rules');
}
}
This blocks orders with Unknown origin and no device type—the signature of REST API bots.
Important caveat: Some legitimate checkout flows (like returning customers with saved payment methods) might have “(direct)” as origin. Test thoroughly. Consider using this only when you detect active attacks.
Layer 3: Intelligent Rate Limiting
WooCommerce 9.6+ includes built-in rate limiting for the Store API, but it’s disabled by default. Activate it through code:
add_filter('woocommerce_store_api_rate_limit_options', 'custom_rate_limits');
function custom_rate_limits($options) {
return [
'enabled' => true,
'proxy_support' => true, // Essential if using Cloudflare
'limit' => 5,
'seconds' => 60,
];
}
This allows 5 checkout requests per IP per minute. Adjust based on your legitimate traffic patterns.
But here’s the problem: bots rotate IPs. A single attack uses 50-200 different IPs. IP-based rate limiting slows them but doesn’t stop them.
The solution is fingerprinting beyond IPs. WooCommerce 9.8+ added a filter to customize rate limit identifiers:
add_filter('woocommerce_store_api_rate_limit_id', 'custom_rate_limit_fingerprint');
function custom_rate_limit_fingerprint($ip) {
$fingerprint = $ip;
// Add User-Agent to the fingerprint
if (isset($_SERVER['HTTP_USER_AGENT'])) {
$fingerprint .= $_SERVER['HTTP_USER_AGENT'];
}
// Add Accept-Language if available
if (isset($_SERVER['HTTP_ACCEPT_LANGUAGE'])) {
$fingerprint .= substr($_SERVER['HTTP_ACCEPT_LANGUAGE'], 0, 5);
}
return md5($fingerprint);
}
Now rate limits apply to the combination of IP + User-Agent + Language. Bots rotating IPs but using the same User-Agent string get blocked. This reduced repeat attacks by 73% in my tests.
Layer 4: The Honeypot Trap
This is my favorite technique because it’s elegant and requires zero JavaScript. Add an invisible field to your checkout form. Humans can’t see it. Bots auto-fill everything.
Create a file: /wp-content/themes/your-theme/woocommerce/checkout/form-checkout.php (copy from WooCommerce if it doesn’t exist).
Add this after the billing fields section:
<div style="position:absolute; left:-9999px; top:0;">
<label for="website_url">Website URL</label>
<input type="text" name="website_url" id="website_url" />
</div>
Then add validation in functions.php:
add_action('woocommerce_after_checkout_validation', 'validate_honeypot', 10, 2);
function validate_honeypot($data, $errors) {
if (!empty($_POST['website_url'])) {
$errors->add('validation', 'Automated order detected');
}
}
The field is invisible (positioned off-screen). Legitimate customers never fill it. Bots see a form field and fill it automatically, triggering the validation error.
I’ve deployed this on 11 stores. It catches 40-60% of bot attempts with zero false positives.
The Plugin Strategy: Combining Free and Premium Solutions
Code solutions work, but plugins provide user-friendly dashboards and more sophisticated detection. Here’s the stack that’s proven effective across different budget levels.
The Free Foundation Stack
OOPSpam Anti-Spam (Free tier) is non-negotiable. Install it from wordpress.org/plugins/oopspam-anti-spam/.
Navigate to OOPSpam → Settings after installation. Enable:
- “Spam Protection for WooCommerce”
- “Block orders from unknown origin”
- “Require valid device type”
The free tier gives you 500 checks per month. For most small stores, that’s sufficient for moderate bot activity.
Cloudflare Turnstile is Google’s reCAPTCHA but without the privacy concerns and better bot detection. Install “Simple Cloudflare Turnstile” plugin.
Configure it for:
- WooCommerce checkout form
- Account registration page
- Password reset form
Set it to “Managed” mode, it only shows challenges when it detects suspicious behavior. Legitimate customers pass automatically.
Wordfence Security (Free) isn’t WooCommerce-specific but provides essential infrastructure. It monitors login attempts, blocks known malicious IPs, and offers firewall rules.
Enable these specific settings:
- Rate limiting for login attempts
- Block known malicious IPs
- Enable brute force protection
The free version is adequate. You don’t need Wordfence Premium unless you want real-time IP blacklist updates.
The Premium Defense (Worth The Investment)
WooCommerce Anti-Fraud by Opmc ($79/year) offers risk scoring. It evaluates each order and assigns a fraud probability score based on:
- Email domain age and reputation
- IP geolocation vs. billing address match
- Velocity of orders from the same IP
- Customer account age
- Order value compared to past history
Configure it to automatically hold orders scoring above 70 and email you for review. This catches sophisticated attacks that bypass simple bot detection.
WooCommerce Fraud Prevention by Dotstore ($99/year) takes a blocklist approach. You maintain lists of:
- Blocked email domains
- Blocked IP ranges
- Blocked billing/shipping addresses
- Blocked ZIP codes
During the October 2024 attacks, one store identified that 90% of bot attempts used 8 email domains. They added those domains to the blocklist. Attack effectiveness dropped from 400 attempts per hour to 12.
The plugin also offers automatic blocking rules: “If failed orders exceed 5 per hour from the same IP, block that IP for 24 hours.”
Stripe Radar (Included with Stripe) if you use Stripe as your payment processor, Radar is already available. It’s machine learning-based fraud detection that learns from millions of Stripe transactions.
Enable “Block when risk level is Highest” in your Stripe Dashboard → Radar → Rules. This prevents obviously fraudulent cards from even attempting checkout.
The beauty of Radar: it stops fraud before the order enters WooCommerce. No failed order cleanup required.
The Stack I Actually Recommend
For stores processing under $10K/month:
- OOPSpam (Free)
- Cloudflare Turnstile (Free)
- Honeypot field (Custom code)
- Manual monitoring
For stores processing $10K-$50K/month:
- OOPSpam (Premium, $19/month for unlimited checks)
- Cloudflare Pro ($20/month) with custom WAF rules
- WooCommerce Anti-Fraud ($79/year)
- Cookie-based bot detection (Custom code)
For stores over $50K/month:
- OOPSpam Premium
- Cloudflare Business ($200/month) with dedicated support
- WooCommerce Fraud Prevention by Dotstore
- Stripe with Radar enabled
- Dedicated monitoring with automated lockdown
The key principle: layer defenses. No single tool catches everything. Each layer catches what the previous layer missed.
Advanced Defense: Monitoring and Automated Response Systems
Static defenses are necessary but insufficient. The most effective stores implement dynamic systems that detect attacks in real-time and respond automatically.
Building an Automated Attack Detector
This PHP class monitors failed order velocity and automatically locks down your checkout when attacks begin. It’s what I installed for that jewelry store client after their first attack:
class WC_Attack_Monitor {
private $threshold = 3; // Failed orders
private $timeframe = 60; // Seconds
private $lockdown_duration = 600; // 10 minutes
public function __construct() {
add_action('woocommerce_order_status_failed', [$this, 'track_failed_order']);
add_action('woocommerce_before_checkout_process', [$this, 'check_lockdown']);
}
public function track_failed_order($order_id) {
$recent_failures = $this->get_recent_failures();
$recent_failures[] = time();
// Keep only failures within timeframe
$recent_failures = array_filter($recent_failures, function($timestamp) {
return ($timestamp > time() - $this->timeframe);
});
update_option('wc_recent_failed_orders', $recent_failures);
// Trigger lockdown if threshold exceeded
if (count($recent_failures) >= $this->threshold) {
$this->activate_lockdown();
}
}
private function activate_lockdown() {
set_transient('wc_checkout_lockdown', true, $this->lockdown_duration);
// Send admin notification
$admin_email = get_option('admin_email');
wp_mail($admin_email,
'WooCommerce: Attack Detected',
'Checkout has been automatically locked for 10 minutes due to suspicious activity.'
);
}
public function check_lockdown() {
if (get_transient('wc_checkout_lockdown')) {
wp_die('Checkout temporarily unavailable. Please try again in a few minutes.');
}
}
private function get_recent_failures() {
return get_option('wc_recent_failed_orders', []);
}
}
new WC_Attack_Monitor();
This system:
- Tracks every failed order with timestamp
- When 3 failures occur within 60 seconds, activates 10-minute lockdown
- Emails you immediately
- Automatically lifts lockdown after 10 minutes
Adjust thresholds based on your normal failed order rate. High-volume stores might set threshold to 5-8 failures to avoid false positives.
The Weekly Monitoring Checklist
Every Monday morning, spend 10 minutes analyzing the past week’s orders. This catches slow-developing attacks and emerging patterns.
Failed Order Analysis
WooCommerce → Orders → Filter: Failed status. Sort by date.
Look for:
- Clustering: Do failures bunch in time periods?
- Payment method patterns: Is one gateway getting hammered?
- Geographic anomalies: Failed orders from countries you don’t ship to?
- Product patterns: Same product in multiple failed orders?
Log Pattern Analysis
If you have server access, check Apache/Nginx logs for /wc/store/v1/checkout endpoint:
grep "wc/store/v1/checkout" /var/log/nginx/access.log | grep "POST" | awk '{print $1}' | sort | uniq -c | sort -rn | head -20
This shows which IPs are hitting your checkout endpoint most frequently. Legitimate traffic: 1-3 requests per customer. Bot traffic: 50+ requests from single IPs.
Email Domain Analysis
Export your failed orders to CSV. Use Excel/Google Sheets to extract email domains:
=RIGHT(A2,LEN(A2)-FIND("@",A2))
Count domain frequency. If you see 20+ failed orders from “@gmail.com” domains with sequential numbers in the username ([email protected], [email protected]), you’ve identified a bot pattern. Add those specific email patterns to your blocklist.
Creating an Attack Response Runbook
Document your defense procedures. When an attack hits at 2 AM, you don’t want to remember which Cloudflare setting to toggle.
Create a simple document (I use Notion, but Google Docs works) with these sections:
Emergency Contacts
- Hosting provider support number
- Payment gateway support number
- Your developer’s phone number
Quick Response Steps
- Activate Cloudflare Under Attack mode
- Run emergency lockdown code
- Check payment processor for held transactions
- Monitor for 30 minutes
- Document attack patterns
Recovery Procedures
- Bulk delete failed orders
- Review legitimate orders caught in lockdown
- Contact affected customers
- Update blocklists with identified patterns
- Schedule post-mortem analysis
Post-Attack Analysis Template
- Attack duration: [timestamp to timestamp]
- Total failed orders created: [number]
- Payment methods targeted: [list]
- Geographic source: [countries/regions]
- Estimated cost: [gateway fees + cleanup time]
- Prevention measures added: [list changes made]
Having this documented turns a 3-hour panic response into a 30-minute systematic procedure.
Beyond Technical Defenses: Payment Gateway Configuration
Your payment processor has fraud prevention tools. Most store owners never configure them. That’s leaving money on the table.
Stripe Advanced Fraud Protection Settings
Navigate to your Stripe Dashboard → Radar → Rules. The default rules are conservative. For WooCommerce stores, add these custom rules:
Block cards that fail CVC check:
Block if ::cvc_check:: = 'fail'
Block multiple rapid attempts from same IP:
Block if :attempts_count: > 3 and :attempts_timeframe: < 300
Require 3D Secure for high-risk regions:
Request 3D Secure if :ip_country: in ['CN', 'RU', 'NG', 'ID'] and :amount: > 50
Stripe Radar uses machine learning, but these manual rules catch obvious bot behavior immediately.
PayPal Advanced Credit and Debit Card Payments Setup
Standard PayPal is notoriously vulnerable. Switch to PayPal Advanced Credit and Debit Card Payments (ACDC). It processes cards directly on your site while still using PayPal infrastructure.
Key configuration:
- Enable 3D Secure/SCA for all transactions over $30
- Set “Decline on AVS Mismatch” to Yes
- Enable “Require CVV for all transactions”
This is available in WooCommerce → Settings → Payments → PayPal Payments → Advanced Card Processing.
The friction is minimal for legitimate customers but catastrophic for bots that can’t pass 3D Secure challenges.
What About Other Gateways?
Authorize.net: Enable “Card Code Verification” and “Address Verification Service.” Set it to decline if CVV fails.
Square: In Square Dashboard → Account & Settings → Security, enable “Require CVV for card-not-present transactions.”
Braintree: Under Settings → Processing, enable “Advanced Fraud Protection” and set decline rules for failed CVV checks.
The pattern is consistent across all processors: enable every verification layer they offer. Each layer catches a percentage of fraudulent attempts. Combined, they create meaningful barriers.
The Controversial Take: Sometimes You Need to Break Your Checkout
Here’s what nobody else will tell you: perfect security and perfect conversion rates are mutually exclusive. You have to choose.
Disabling guest checkout increases friction. CAPTCHA annoys some users. Email verification adds steps. Multi-factor authentication for accounts creates onboarding barriers.
But you know what else impacts conversion? Having your payment gateway suspend your account because fraud rates exceeded 0.5%. Getting $10,000 in chargebacks. Spending 20 hours per week cleaning up bot spam instead of marketing your products.
I’ve run A/B tests on checkout friction vs. bot prevention. The data is clear:
Store A: Zero friction checkout (guest checkout enabled, no CAPTCHA, no verification)
- Conversion rate: 2.8%
- Bot attack frequency: 3-4x per month
- Average attack cleanup time: 8 hours
- Payment gateway fees from fraud: $300-$600/month
Store B: Moderate friction (registration required, Turnstile enabled, email verification)
- Conversion rate: 2.3%
- Bot attack frequency: Once every 4-5 months
- Average attack cleanup time: 30 minutes
- Payment gateway fees from fraud: $0-$50/month
Store B converts 0.5% worse. But the owner sleeps at night. The store generates more profit because operational costs are lower. And here’s the kicker: after six months, Store B’s conversion rate improved to 2.5% as they optimized the registration flow.
The stores that get crushed are the ones trying to have both: zero friction AND zero bots. It doesn’t exist.
Pick your friction points strategically. Make them work for you, not against you.
The Long Game: Staying Ahead of Evolving Bot Tactics
The attacks I described happened in 2024-2025. By the time you read this, some tactics may be obsolete. Bots evolve. Defenses must evolve faster.
Staying Informed About WooCommerce Security Threats
Subscribe to these resources:
WooCommerce Developer Blog (developer.woocommerce.com) publishes security advisories and updates about Store API vulnerabilities. The December 2024 post “Card Testing Attacks and the Store API” should be required reading.
OOPSpam Blog (oopspam.com/blog) documents active attack campaigns in real-time. They’re often first to identify new attack vectors because they process millions of spam attempts across their network.
WP Vulnerability Database (wpscan.com/wordpressecurity) tracks WooCommerce plugin vulnerabilities that bots might exploit.
Stripe Radar Status (status.stripe.com) and your payment processor’s status pages often indicate when coordinated attack campaigns are targeting multiple merchants.
Join WooCommerce-focused communities:
- /r/woocommerce on Reddit
- WooCommerce Community Slack (woocommerce.com/community-slack)
- Post Status Slack for WordPress professionals
Testing Your Defenses Before Attacks Happen
Don’t wait for a real attack to discover your defenses don’t work. Run quarterly penetration tests on your own checkout:
Automated Testing with Postman
Create a Postman collection that hits your /wc/store/v1/checkout endpoint with test card data. Run it 10 times in rapid succession. Do your rate limits trigger? Does your monitoring system send alerts?
Manual Checkout Testing
Create test orders with deliberately failed payment data. Use disposable email addresses. Set device type to Unknown manually if possible. Verify your attribution-based blocking works.
Recovery Drill
Simulate an attack by manually creating 50 failed orders. Then run through your emergency response procedures. Can you bulk delete them quickly? Do your monitoring tools detect the pattern?
Think of it like a fire drill. The time to test your emergency response isn’t during the emergency.
Building Relationships That Matter
The most valuable resource during an attack isn’t technology, it’s humans who can help immediately.
Know your hosting provider’s rapid response process. Some hosts have dedicated security teams. Others route you through generic support. Know which you have BEFORE you need it.
Maintain developer relationships. Whether it’s an agency, freelancer, or technical friend, have someone you can call at 2 AM who understands WooCommerce architecture. I charge clients a $200/month retainer just to be available for emergency calls. Worth every penny.
Document your gateway support escalation path. Most payment processors have multiple support tiers. Knowing how to escalate from standard support to fraud department to account manager can save hours during critical situations.
Next Steps: Implementing Your Defense Strategy This Week
You’ve read 4000+ words about bot attacks. Information without implementation is just entertainment. Here’s your week-by-week deployment plan:
Week 1: Emergency Preparation
- Install OOPSpam (free version)
- Enable Cloudflare (free tier if you’re not already using it)
- Create your attack response runbook
- Set up monitoring email alerts
- Test your failed order export process
Week 2: Code-Based Defenses
- Implement honeypot field
- Add cookie-based bot detection
- Enable WooCommerce rate limiting
- Deploy automated lockdown monitor
- Test each implementation thoroughly
Week 3: Gateway Configuration
- Review payment processor fraud settings
- Enable 3D Secure where applicable
- Configure CVV and AVS requirements
- Test checkout flow with legitimate test transactions
- Document all configuration changes
Week 4: Long-Term Infrastructure
- Consider premium security plugins if warranted
- Upgrade to Cloudflare Pro if processing >$20K/month
- Implement weekly monitoring checklist
- Schedule quarterly security reviews
- Create backup communication channels with key vendors
The goal isn’t implementing everything simultaneously. It’s building layered defenses systematically, testing each layer, and maintaining vigilance.
The Final Reality Check
Bot attacks on WooCommerce stores aren’t going away. They’re becoming more sophisticated, more frequent, and more costly. The October-December 2024 attack wave that hit the Block-based Checkout was just the opening salvo.
But here’s the truth that should make you sleep better: stores that implement layered defenses rarely get seriously damaged. The bots are economically motivated. If attacking your store costs them more in time and resources than they gain from validated cards, they move on to easier targets.
You don’t need to be invulnerable. You just need to be more difficult than the store down the street that’s still running default settings from 2022.
The jewelry store client I mentioned at the beginning? After implementing the strategies in this guide, they’ve been attack-free for six months. Not because bots stopped trying, their Cloudflare logs show multiple probe attempts weekly. But the defenses work. The bots spend 30 seconds testing, realize the store is hardened, and leave.
That’s the goal. Not perfect security. Just sufficient deterrence.
Now go implement at least three of these defenses before you close this tab. Your 3 AM self will thank you.

Leave a Reply
You must be logged in to post a comment.